Process of Configuring, Verifying Trunking on Cisco Switches
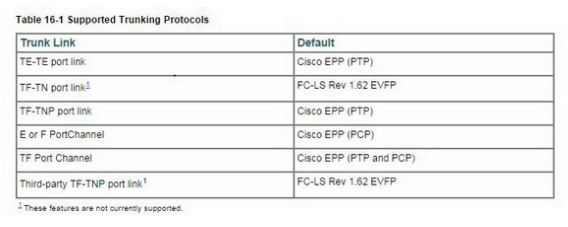
Describe the Process of Configuring and Verifying T runking on Cisco Switches Knowing about trunking of the cisco switches is very important. The reason behind is, that cisco is very famous and the switches which are offered by cisco are used in the offices and work places very frequently. The trunking protocol is critical for trunking operations on the ports. The protocols empower the accompanying exercises: • Dynamic arrangement of operational trunk mode. • Selection of a typical set of trunk-permitted VSANS. • Detection of a VSAN confuse over ISL. Here are the commands used for that: Of course, the trunking protocol is empowered on E ports and debilitated on F ports. In the event that the trunking protocol is impaired on a switch, no port on that switch can apply new trunk arrangements. Existing trunk designs are not influenced. The TE port keeps on functioning in trunk mode, yet just backings activity in VSANS that it arranged with formerly (when...


